Implementing Mandatory Access Control with SELinux , To conquer constraints and to increase the safety mechanisms provided by using wellknown ugo/rwx permissions and get entry to manipulate lists.
The USA National Security Agency (NSA) devised a flexible Mandatory Access Control (MAC) approach called SELinux on the way to restrict amongst different things.
The ability of tactics to get right of entry to or carry out different operations on gadget items to the least permission feasible, whilst still taking into account later adjustments to this version.

Implementing Mandatory Access Control with SELinux
Another popular and broadly-used MAC is AppArmor, which similarly to the features provided with the aid of SELinux.
consists of a gaining knowledge of mode that allows the device to “learn” how a particular software behaves, and set limits with the aid configuring profiles for safe application utilization.
In CentOS 7, SELinux is included into the kernel itself and is enabled in Enforcing mode by using default, in place of openSUSE and Ubuntu which use AppArmor.
In this newsletter we can explain the essentials of SELinux and AppArmor and how to use any such gear for your gain relying on your preferred distribution.
Implementing Mandatory Access Control ,Introduction to SELinux and Use it on CentOS
Security Enhanced Linux can perform in extraordinary ways:
- Enforcing: SELinux denies get admission to primarily based on SELinux coverage rules, a fixed of tips that manage the safety engine.
- Permissive: SELinux does now not deny get right of entry to, but denials are logged for actions that would were denied if going for walks in implementing mode.
Implementing Mandatory Access Control with SELinux ,SELinux can also be disabled. Although it is not an operation mode itself, it’s far nonetheless an choice.
However, mastering a way to use this tool is higher than just ignoring it. Keep it in thoughts!
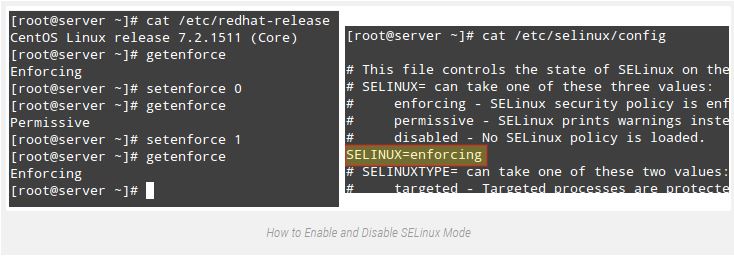
To show the modern-day mode of SELinux, use getenforce. If you need to toggle the operation mode, use setenforce zero (to set it to Permissive) or setenforce 1 (Enforcing).
Since this variation will now not continue to exist a reboot, you will want to edit the /and many others/selinux/config record and set the SELINUX variable to both imposing, permissive, or disabled so that it will gain staying power across reboots:
On a facet notice,
if getenforce returns Disabled, you will need to edit /etc/selinux/config with the desired operation mode and reboot. Otherwise, you may no longer be capable of set (or toggle) the operation mode with setenforce.
One of the standard uses of setenforce consists of toggling between SELinux modes to troubleshoot an software that is misbehaving or no longer working as expected.
If it works after you set SELinux to Permissive mode, you could be confident you’re looking at a SELinux permissions difficulty.
Two conventional cases in which we can maximum possibly need to deal with SELinux are:
- Changing the default port in which a daemon listens on.
- Setting the DocumentRoot directive for a virtual host outside of /var/www/html.
Let’s check these instances the usage of the following examples.
EXAMPLE 1: Changing the default port for the sshd daemon
Implementing Mandatory Access Control with SELinux, One of the primary factor most device directors do if you want to comfy their servers is change the port in which the SSH daemon listens on, broadly speaking to deter port scanners and external attackers.
To do this, we use the Port directive in /and many others/ssh/sshd_config followed via the brand new port number as follows (we will use port 9999 in this situation):
Port 9999After trying to restart the carrier and checking its status we will see that it didn’t start:
# systemctl restart sshd
# systemctl status sshd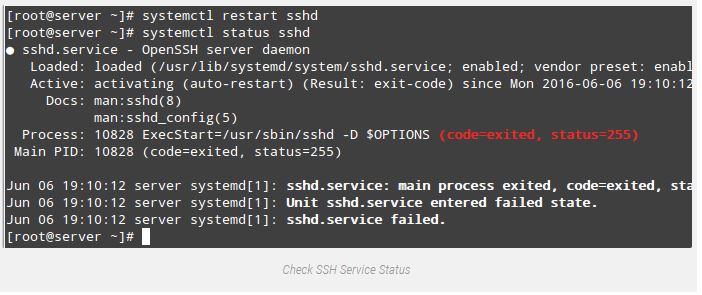
If we take a look at /var/log/audit/audit. Log, we can see sshd was avoided from beginning on port 9999 by means SELinux due to the fact that could be reserved port for JBoss Management carrier:
# cat /var/log/audit/audit.log | grep AVC | tail -1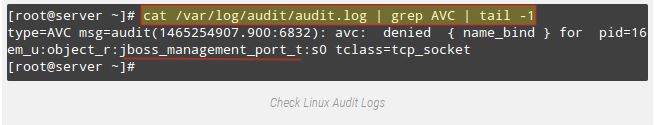
At this factor
most of the people might possibly disable SELinux but we gained’t. We will see that there’s a way for SELinux, and sshd listening on a distinct port, to live in harmony collectively.
Make certain you have the policycoreutils-python bundle hooked up and run:
# yum install policycoreutils-pythonTo view a list of the ports where SELinux permits sshd to pay attention on.
In the subsequent photograph we also can see that port 9999 changed into reserved for any other service and consequently we can’t use it to run another carrier at the moment:
# semanage port -l | grep sshOf path
we may want to select another port for SSH, but if we are positive that we will now not need to use. this specific system for any JBoss-associated offerings, we are able to then modify the prevailing SELinux rule and assign that port to SSH alternatively:
this specific system for any JBoss-associated offerings, we are able to then modify the prevailing SELinux rule and assign that port to SSH alternatively:
this specific system for any JBoss-associated offerings, we are able to then modify the prevailing SELinux rule and assign that port to SSH alternatively:
# semanage port -m -t ssh_port_t -p tcp 9999After that, we are able to use first semanage command test if the port became efficaciously assigned, or the-lC alternatives:
# semanage port -lC
# semanage port -l | grep ssh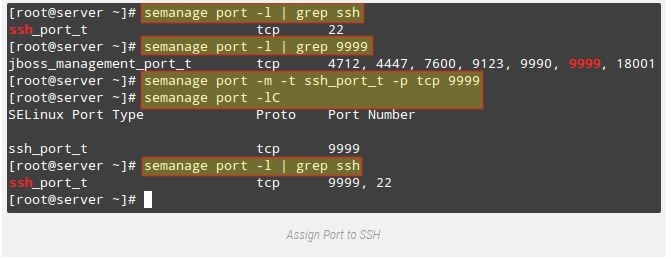
We can now restart SSH and connect with the provider the usage of port 9999. Note that this change WILL continue to exist a reboot.
EXAMPLE 2: Choosing a DocumentRoot outside /var/www/html for a virtual host
If you want to set up a Apache virtual host the use of a listing aside from /var/www/html as DocumentRoot:
DocumentRoot “/websrv/sites/gabriel/public_html”Apache will refuse to serve the content because the index.Html has been labeled with the default_t SELinux type, which Apache can’t get admission to:
# wget http://localhost/index.html
# ls -lZ /websrv/sites/gabriel/public_html/index.html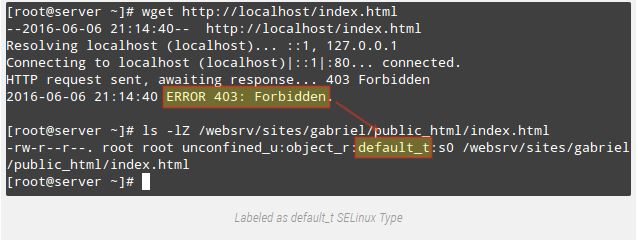
As with the preceding example, you could use the following command to verify that that is certainly a SELinux-related problem:
# cat /var/log/audit/audit.log | grep AVC | tail -1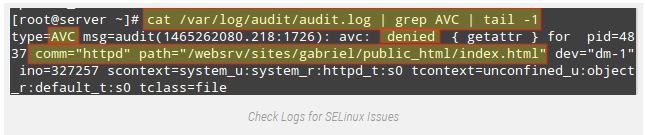
To change the label of /websrv/sites/gabriel/public_html recursively to httpd_sys_content_t, do:
# semanage fcontext -a -t httpd_sys_content_t "/websrv/sites/gabriel/public_html(/.*)?"The above command will furnish Apache study-handiest access to that listing and its contents.
Finally, to use the policy (and make the label exchange effective at once), do:
# restorecon -R -v /websrv/sites/gabriel/public_htmlNow you must be capable of get entry to the directory:
# wget http://localhost/index.html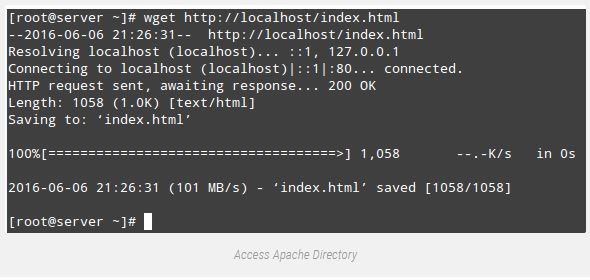
Introduction to AppArmor and How to Use it on OpenSUSE and Ubuntu
The operation of AppArmor is based totally on profiles described in plain textual content documents in which the allowed permissions and get right of entry to manage policies are set.
Profiles are then used to area limits on how programs interact with methods and documents in the device.
A set of profiles is provided out-of-the-box with the running machine, while others can be installed place both automatically through programs when they’re mounted or manually by means of the gadget administrator.
Like SELinux, AppArmor runs profiles in modes. In put in force mode, applications are given the minimal permissions which can be vital for them to run.
whereas in whinge mode AppArmor permits an software take constrained moves and saves the “proceedings” resulting from that operation a log.
These logs will show thru lines with the word audit in them mistakes that could arise ought to the profile be run put in force mode.
Thus, you may try out an application in whinge mode and modify its conduct before going for walks it underneath AppArmor in enforce mode.
The cutting-edge popularity of AppArmor may be proven the use of:
$ sudo apparmor_status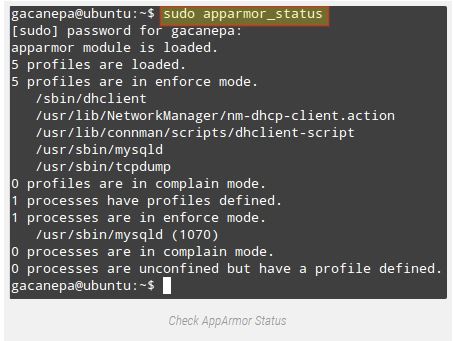
The image above
suggests that the profiles /sbin/dhclient, /usr/sbin/, and /usr/sbin/tcpdump are in enforce mode (that is real by default in Ubuntu).
Since no longer all programs encompass the related AppArmor profiles, the apparmor-profiles package, which gives other profiles which have now not been shipped by means of the applications they offer confinement for.
By default, they’re configured run in complain mode that system directors can check them and pick out which ones are desired.
We will make use apparmor-profiles due to fact writing our own profiles is out of the scope the LFCS certification.
However, given that profiles are plain textual content documents, you may view them and create your personal profiles inside destiny.
AppArmor profiles are stored inner /etc/apparmor.D. Let’s test the contents of that listing before and after putting in apparmor-profiles:
$ ls /etc/apparmor.d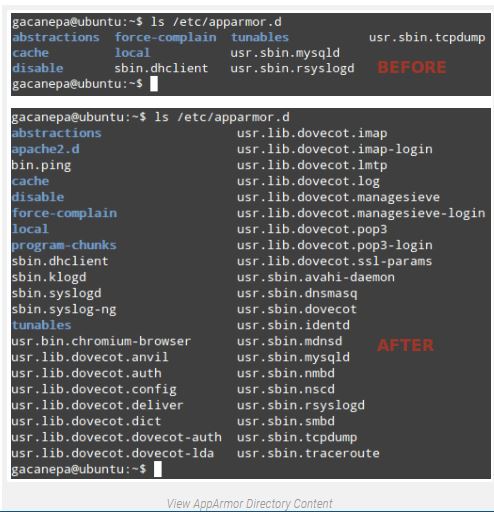
If you execute sudo apparmor_status once more, you may see a longer list of profiles in bitch mode. You can now carry out the subsequent operations:
To transfer a profile currently in implement mode to complain mode:
$ sudo aa-complain /path/to/fileAnd the alternative manner round (bitch –> implement):
$ sudo aa-enforce /path/to/fileWildcards are allowed within the above instances. For example,
$ sudo aa-complain /etc/apparmor.d/*Will vicinity all profiles inside /and so on/apparmor.D into complain mode, while
$ sudo aa-enforce /etc/apparmor.d/*Will switch all profiles to enforce mode.
To totally disable a profile, create a symbolic link in the /and many others/apparmor.D/disabled directory:
$ sudo ln -s /etc/apparmor.d/profile.name /etc/apparmor.d/disable/For more records on AppArmor, please check with the legitimate AppArmor wiki and to the documentation provided by using Ubuntu.
Implementing Mandatory Access Control ,Summary
In this article we’ve gone via the basics of SELinux and AppArmor, two well-known MACs. When to use one or the opposite? To avoid difficulties, you could want to remember sticking with the one that incorporates your selected distribution.
In any occasion, they may help area restrictions strategies and get entry to system assets to growth security your servers.
Do you’ve got any questions, feedback, or guidelines about this newsletter? Feel unfastened to let us realize the use of the shape under. Don’t hesitate to let us recognise if you have any questions or remarks.