
Set Up SSH Key Secure Shell is the most broadly-used manner of logging into a far off Linux server (or computer). By using this device, you gain get entry to to the command line on a far flung system, via a comfortable tunnel. Out of the field, you’ll be triggered to type the faraway user’s password. Although that is nevertheless more comfy than the usage of the older methods (which includes telnet), it is able to be made even greater comfy with SSH Key Authentication.
Set Up SSH Key What is Key Authentication?
Set Up SSH Key Understanding Key Authentication is truly pretty simple. Imagine you’ve got a lock and the best manner to open that lock is with a particular key that the lock knows belongs to you. How does the lock recognise the important thing belongs to you? Because the key incorporates a signature that is particular to you. Within the lock there may be an identical signature the key makes use of for evaluation. Should the signatures suit, they lock will open. Should the key suit, however the signatures now not match, the lock gained’t open.
That’s the basis for SSH Key Authentication. How it works in actual life is that you create a key pair (which incorporates a private and public key), and copy the public key to the server you need to log into. If you try to login with key authentication, and the server doesn’t have the public key that suits your personal key, it received’t allow you access.
Let’s make this work.
Set Up SSH Key Generating an SSH Key Pair
Open a terminal window on your computer.
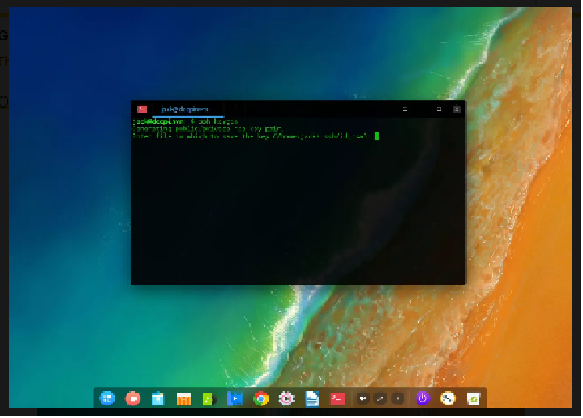
Issue the command:
ssh-keygenGive the important thing a name and place (go with the default through the usage of Enter/Return to your keyboard).
2. Enter and verify a passphrase for the key (make sure this passphrase is strong and unique)
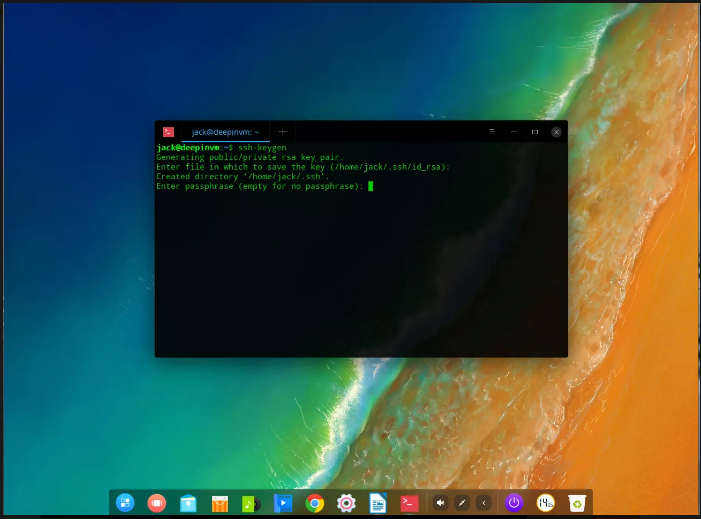
You now have an SSH key pair. These two documents will be discovered in ~/.Ssh and might be named:
- id_rsa – The private key.
- id_rsa.pub – The public key.
Copy Your Public Key to the Remote Machine
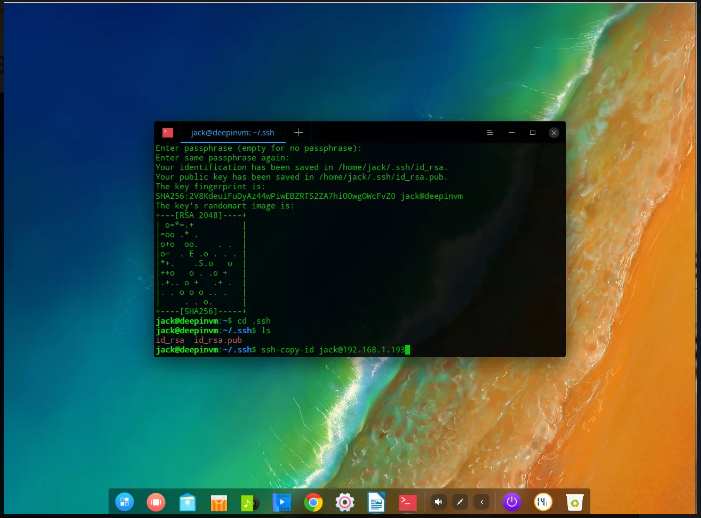
Set Up SSH Key Next you have to replica the public key document to the far flung system you want to log into. This may be finished with the command:
ssh-copy-id USER@REMOTE_IPWhere USER is a username on the far flung system and REMOTE_IP is the IP deal with of the far flung gadget.
If this is the primary time you’ve comfy shelled into the remote machine, you may be prompted to kind yes to maintain with the relationship, otherwise you’ll be triggered to type the consumer password on the far off device. Once you’ve efficaciously typed your far off password, the key can be copied and also you’re geared up to test the relationship.
Set Up SSH Key Testing The Connection
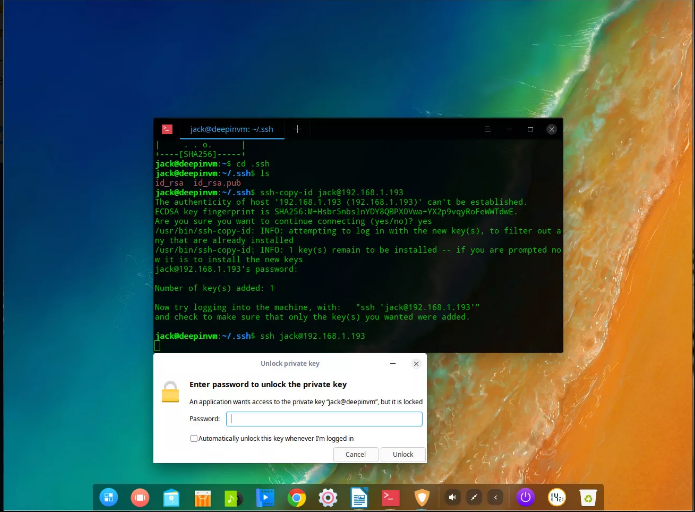
Test the connection by issuing the command:
ssh USER@REMOTE_IPWhere USER is a username at the far off system and REMOTE_IP is the IP address of the remote device. Instead of being brought about for the user password, you’ll be prompted for the SSH key pair passphrase. Once you’ve typed the precise key passphrase, you’ll be allowed get admission to to the far off system. Congratulations, SSH Key Authentication is up and strolling.
Set Up SSH Key Disabling Password Authentication
You can take this one step in addition by way of disabling password authentication. With this configuration in region, the most effective way to benefit get entry to to the far off system is from a gadget containing the private key from the matching pair. In different words, no key pair, no access.
To disable password authentication, log into the far flung gadget and issue the command:
sudo nano /etc/ssh/sshd_configIn this file, look for the line:
#PasswordAuthentication yesChange that line to:
PasswordAuthentication noSave and close the file. Restart SSH with the command:
sudo systemctl restart sshd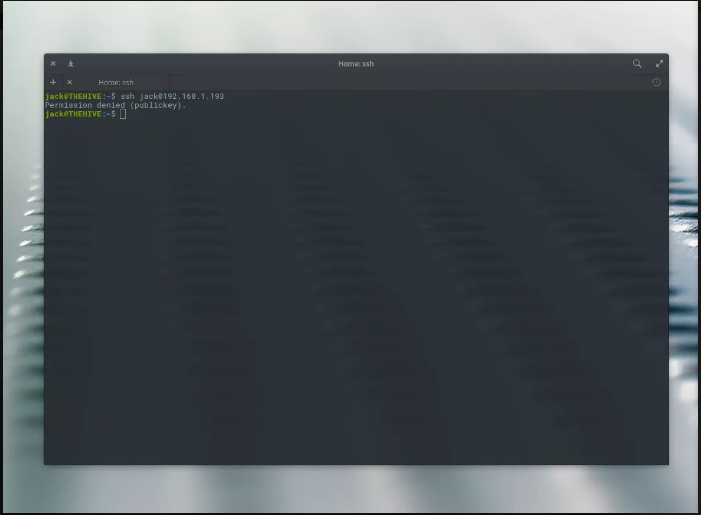
Set Up SSH Key Now, if you try and log into that remote device from any desktop (or server) that doesn’t include the personal key, get entry to may be denied.
Congratulations, you have efficaciously made logging into your far off Linux machine more secure with SSH.




